Sonos takes a great product and makes it more affordable. Reviewer Jim Buzbee has finally found a wireless audio player that he will be sorry to part with.
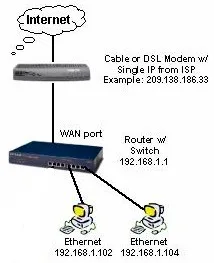
Everyone with a high-speed Internet connection needs a router. So why not learn how to choose the one that best meets your needs? We’ve updated and expanded our classic Hardware Router Need To Know to help you do just that!
Intel has decided it wants to play in the SOHO/SMB NAS market and produces a first product that should get it into the game.
These two products take very different approaches to enhancing Skype phoning. Ed Tittel and Justin Korelc put the Iogear USB VoIP Skype Calling Kit and TRENDnet ClearSky Bluetooth VoIP Kit through their paces
The nattering nabobs of negativity are at it again, telling us to stay away from the latest and greatest in wireless networking technology. Tim Higgins thinks they’re just a bunch of weenies.
Spring may mean the return of flowers, birds and bees to those in northern climes. But to Tim Higgins, it means an annual pilgrimage to Sin City to check out what’s new in Networking. Come along for a round-up of early-bird announcements and news.
A $100 networked media adapter handling music, photos and video sure got our attention. But Jim Buzbee found that Buffalo made too many compromises to get under that magic hundred dollar mark.
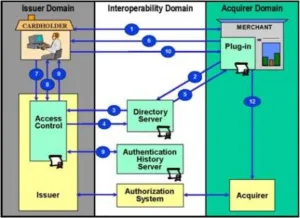
3D Secure is the new protocol being developed by the main players in the credit card payments business to try to combat credit card fraud. The kicker, however, is that it shifts responsibility for the cost of fraud from the acquirers (merchants and their banks) to us – consumers and our banks. Pat McKenna shows you just what 3DS is all about.
P2P may have have unsavory connotations now, but the technology will probably be soon incorporated into HD video distribution. Tim Higgins turns up the heat on seven routers to see if they have what it takes.
As wireless broadband access becomes more ubiquitous, is it becoming possible for a businessperson to conduct his everyday work, at high speed, out in the middle of nowhere? Scott Fulton reports from the wilds of Indiana.
We rely on security walls to keep intruders out, while leaving gates so that we can get in and out ourselves. Most hacking involves trying to break down or otherwise sneak past these gates, but the easiest way to get in is to convince the gatekeeper to open the door. In networking security circles, this is known as Social Engineering, and it’s something you need to understand.